
Imagine you have a ledger with a billion transactions. Checking if one of them was changed means downloading and comparing the whole thing? That’s slow, expensive, and unnecessary. Enter the Merkle tree - a clever system that lets you prove data hasn’t been tampered with using just a few lines of code and a single hash. It’s not magic. It’s math. And it’s why Bitcoin and Ethereum can run on ordinary computers instead of supercomputers.
How a Merkle Tree Works
A Merkle tree is built from the bottom up. Each transaction or data block gets hashed - turned into a unique 64-character string using SHA-256. These hashes become the leaf nodes of the tree. Then, pairs of these hashes are combined, hashed again, and turned into parent nodes. This keeps happening until you reach the top: one single hash called the Merkle root. That root is the fingerprint of everything below it. Change one letter in one transaction? The leaf hash changes. That changes the parent hash. Then the grandparent. Then the root. The entire tree collapses into a new value. No guessing. No doubt. The root tells you instantly: something’s different. This isn’t just theory. Bitcoin uses Merkle trees in every block. The block header contains the Merkle root. Miners don’t need to store every transaction ever made to verify new ones. They just need the root and a small proof. That’s how your phone wallet can confirm a payment without downloading the whole blockchain.Why It’s Secure
The security comes from three properties of cryptographic hashing: collision resistance, preimage resistance, and the avalanche effect. Collision resistance means it’s practically impossible to find two different inputs that produce the same hash. Preimage resistance means you can’t reverse-engineer the original data from the hash. And the avalanche effect? Change one bit in the input, and half the bits in the output flip. That’s what makes tampering obvious. These aren’t theoretical guarantees. They’re built into SHA-256, the hash function used by Bitcoin since day one. No one has broken it. Not even with today’s most powerful supercomputers. That’s why Merkle trees are trusted to protect trillions of dollars in value.Proofs Without the Data
Here’s where Merkle trees get really powerful: you don’t need the full dataset to prove something is true. Let’s say you want to prove transaction #4,287,912 is part of a block. You don’t send the whole block. You send just the hashes along the path from that transaction up to the root. This is called a Merkle proof. It’s typically 10-20 hashes long, even for a block with 5,000 transactions. That’s less than 2KB of data. A node receiving this proof can recompute the path. If the final hash matches the Merkle root, the transaction is confirmed. No full ledger needed. No trust. Just math. This is why light wallets exist. Your phone doesn’t store the blockchain. It just asks a full node: “Is this transaction in the latest block?” The node sends a tiny proof. Your phone checks it. Done. No download. No delay.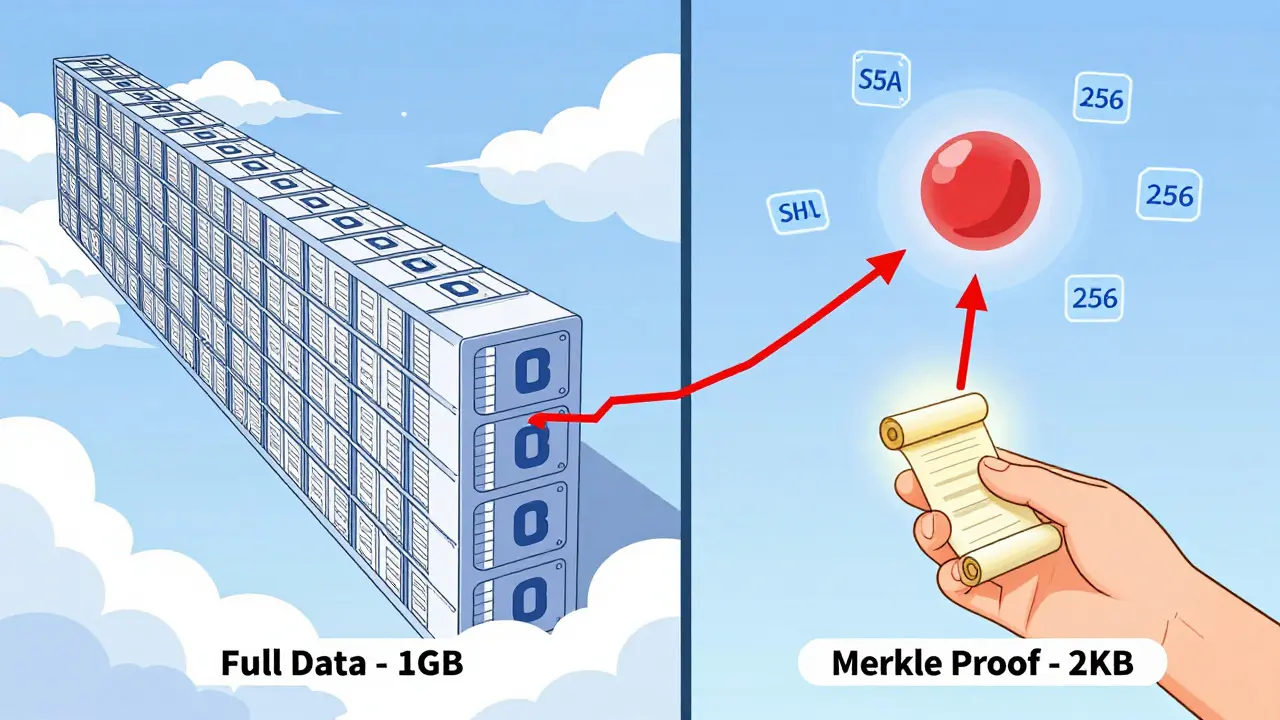
Membership and Non-Membership Proofs
Merkle trees can prove two things: that something is in the set, and that it’s not. Membership proof? Easy. Send the path to the root. If it checks out, the item exists. Non-membership? Trickier, but still possible. You can prove an item is missing by showing the hashes of its immediate neighbors - the closest items that *are* in the tree. If your target isn’t between them, and the path still leads to the root, it’s not there. This is used in blockchain state verification and access control systems. A wallet can prove you don’t own a specific NFT without revealing your whole portfolio. This is critical for privacy. You’re not exposing your entire history. Just the minimum needed to prove your claim.Zero-Knowledge and Merkle Trees
Merkle trees are the backbone of zero-knowledge proofs (ZKPs) in modern blockchains. ZKPs let you prove you know something - like your private key or your balance - without revealing it. In systems like zk-SNARKs or zk-Rollups, your account state is stored in a Merkle tree. When you make a transaction, you generate a proof that says: “I own this account, I have enough funds, and I’m authorized to spend them.” The Merkle root proves the state. The ZKP proves the action. Together, they let you verify transactions without revealing balances, addresses, or transaction history. This is how privacy coins like Zcash work. It’s how Ethereum’s Layer 2 networks scale without compromising security. And it’s why companies are using Merkle trees for confidential enterprise databases - proving data integrity without exposing sensitive records.Real-World Impact: Solana’s State Compression
Solana took Merkle trees further. They used them for state compression - storing account data in Merkle trees instead of on-chain. Before, minting one billion NFTs cost 12 million SOL in storage fees. With Merkle trees and state compression, that dropped to 507 SOL. How? Instead of storing each NFT’s metadata on-chain, they store a single Merkle root. Each NFT gets a proof of existence. When someone buys or transfers it, they verify the proof against the root. The actual data? Stored off-chain. The root? On-chain. The security? Full. This isn’t a gimmick. It’s a game-changer. It means blockchains can handle millions of users without exploding in size. And it’s only possible because Merkle trees let you prove presence with minimal data.
Limitations and Risks
Merkle trees aren’t perfect. Their security depends entirely on the hash function. If SHA-256 is broken - say, by a quantum computer - the whole system collapses. That’s why researchers are already testing post-quantum hash functions like SHA-3 and SPHINCS+ for future Merkle tree designs. There’s also a privacy leak risk. While the data itself is hidden, the structure of the tree can reveal patterns. If you know the Merkle tree has 1,000 leaves, and you see a proof with 10 hashes, you know the item is near the bottom. If you see many proofs from the same branch, you might infer relationships between accounts. Advanced systems now add blinding factors - random values mixed into hashes - to obscure these patterns. But it adds complexity. Most blockchains still rely on basic Merkle trees because they’re simple, fast, and secure enough.Why It Matters for the Future
Merkle trees are everywhere in decentralized systems. They’re in Bitcoin, Ethereum, Filecoin, IPFS, and even in IoT devices that need to verify firmware updates without full downloads. They solve the core problem of trust in distributed systems: how do you know something is true without trusting the source? The answer isn’t more data. It’s less. Just the right proof. As data grows - billions of sensors, millions of transactions per second - Merkle trees will keep scaling. Their verification time grows logarithmically. Double the data? Add one more layer to the tree. Verification time barely changes. That’s why they’ll outlast trends. They’re not flashy. They’re not AI. But they’re the quiet foundation that makes decentralized systems possible. Without Merkle trees, blockchain would be slow, expensive, and unusable for anything beyond small experiments.Final Thought
Merkle trees don’t make blockchain secure by themselves. But they make it *practical*. They turn an impossible problem - verifying a billion records - into a task that fits in a smartphone message. That’s the power of smart design. Simple math. Big impact.What is a Merkle root in blockchain?
The Merkle root is the single hash at the top of a Merkle tree that represents the entire set of transactions in a block. It’s created by recursively hashing pairs of transaction hashes until only one hash remains. Any change to any transaction will change the Merkle root, making it a tamper-evident fingerprint of the block’s data.
Can Merkle trees be used for data that’s not in blockchain?
Yes. Merkle trees are used in distributed file systems like IPFS, version control systems like Git, and enterprise databases to verify data integrity without transferring full files. They’re ideal for any system where you need to prove a file or record hasn’t been altered, especially across networks with limited bandwidth.
How do Merkle trees reduce bandwidth usage?
Instead of sending an entire block of thousands of transactions, a node only needs to send the Merkle proof - a short list of hashes leading from a specific transaction to the root. For a block with 10,000 transactions, this proof is typically 14-16 hashes long, or under 2KB. That’s 1,000x less data than sending the full block.
Are Merkle trees vulnerable to quantum computers?
The security of current Merkle trees relies on SHA-256, which could be broken by large-scale quantum computers using Shor’s or Grover’s algorithms. While Grover’s algorithm only offers a quadratic speedup (making brute force harder but not impossible), researchers are already developing quantum-resistant hash functions like SPHINCS+ and LMS to replace SHA-256 in future Merkle tree implementations.
Why not just use a single hash of all data instead of a tree?
A single hash of all data would work for verifying the whole dataset - but not for proving individual items. If you want to prove one transaction is part of a million-record set, you’d have to send the entire dataset. Merkle trees solve this by letting you prove membership with a small, fixed-size proof, regardless of total data size.


Comments
Jennah Grant
Merkle trees are the unsung heroes of blockchain scalability. You don't need to download the whole chain to verify a transaction-just a tiny proof. That’s why light wallets exist. The math is elegant, the efficiency is insane, and it’s been battle-tested for over a decade.
SHA-256 isn’t perfect, but it’s still standing. Quantum threats? Yeah, we’re thinking about it. But for now, this is how the world’s largest decentralized ledger stays lean.
And honestly? It’s the reason your phone can do crypto at all.
Dave Lite
Bro this is 🔥. Merkle trees are literally the reason I can check my ETH balance on my dumbphone without my battery dying. Imagine if every wallet had to sync the whole chain? We’d all be using 1990s laptops.
And the non-membership proofs? Mind blown. You can prove you don’t own an NFT without showing your whole portfolio. That’s privacy on steroids. 🤯
Tracey Grammer-Porter
I love how this breaks down something so technical into something you can actually feel. It’s not just about hashes and trees-it’s about making trust accessible. Like, your grandma could understand this if you explained it right.
And the fact that Solana cut storage costs by 99.9%? That’s not optimization, that’s magic. Real magic.
Keep explaining stuff like this. We need more of it.
jim carry
Let me stop you right there. You’re oversimplifying. Merkle trees are NOT secure. They’re a glorified linked list with hashes. If someone controls the node you’re querying, they can feed you a fake proof. You’re trusting the messenger. That’s not security, that’s wishful thinking.
And don’t even get me started on ZKPs. Those are just math tricks dressed up as religion. You think your privacy is protected? You’re just giving your data to someone else’s algorithm. Wake up.
Don Grissett
Yall act like merkle trees are some new invention. Nah. This is just hash chains with extra steps. I’ve seen this in git since 2005. Blockchain folks just repackaged it and slapped a crypto label on it.
Also, SHA-256? That’s old news. Even my toaster has better crypto now. We need to move on. This is like using dial-up and calling it 5G.
Katrina Recto
Proofs without the data is the whole point. Why carry the whole library when you just need one page? Merkle trees make that possible. Simple. Clean. Efficient. No fluff. No trust. Just math.
That’s all you need.
Tiffani Frey
It’s fascinating how such a simple, recursive structure-each node being the hash of its children-can scale to billions of records with logarithmic verification complexity. The elegance lies in its symmetry: every leaf contributes equally to the root, and every root validates every leaf.
And yet, we rarely pause to appreciate how this design elegantly decouples storage from verification. It’s not just efficient-it’s philosophically beautiful. The data is distributed; the trust is centralized only at the root. A quiet revolution in distributed systems.
kris serafin
Merkele trees = 🤖🧠💡
Imagine your phone checking a transaction without downloading 800GB of blockchain data. That’s not tech, that’s wizardry. And it’s all because someone decided to stack hashes like LEGO bricks.
Also, Solana’s state compression? That’s the future. NFTs on steroids. 🚀
Jordan Leon
The Merkle root functions as a cryptographic commitment-a single point of truth that binds an entire dataset. Its power lies not in its complexity, but in its minimalism. It allows for verifiable integrity without transparency. This is the essence of decentralized trust: you need not know everything to know that something is true.
It is not a solution to the problem of trust, but a solution to the problem of verifying trust without requiring it.
Allen Dometita
So basically, it’s like having a receipt for your entire grocery cart, but you only need the receipt to prove you bought the bananas. No need to show the whole fridge.
That’s genius. And Solana saving millions in fees? That’s the kind of thing that makes blockchain actually useful. Not just crypto bros yelling about mooning.
Also, if you’re still using a full node in 2025, you’re doing it wrong 😎
Brittany Slick
This is the kind of quiet, brilliant engineering that changes the world without anyone noticing. No hype. No ads. Just math doing its job. I love it.
It’s like the blockchain equivalent of a perfectly tuned violin-simple, elegant, and capable of producing symphonies from silence.
greg greg
Let’s be real here-Merkle trees are only as good as the hash function underneath them, and SHA-256, while currently unbroken, is not immune to mathematical advances, especially when you consider that Grover’s algorithm theoretically reduces the security of a 256-bit hash to 128-bit equivalent, which, while still computationally infeasible today, is a non-trivial reduction that must be accounted for in long-term cryptographic planning, particularly when considering that quantum computing hardware is advancing faster than most people realize, and while current quantum systems are noisy and error-prone, the trajectory of development suggests that fault-tolerant quantum computers capable of executing Grover’s algorithm on SHA-256 could emerge within the next 15 to 30 years, which means that blockchain systems relying on Merkle trees today may need to migrate to post-quantum hash functions like SPHINCS+ or LMS or even SHA-3 in the near future to maintain their security guarantees, and this transition will not be trivial because it requires hard forks, backward compatibility considerations, and widespread adoption across heterogeneous networks, which is why it’s critical that research into quantum-resistant Merkle tree implementations is not just theoretical but actively funded and integrated into protocol development roadmaps now, not when the threat becomes imminent, because once the damage is done, you can’t unbreak a blockchain.
Denise Paiva
Everyone’s acting like Merkle trees are some revolutionary breakthrough. Newsflash: it’s just a binary tree with hashes. We’ve had this in distributed systems since the 80s. Blockchain people just found a new place to slap a logo on old tech.
And don’t get me started on ZKPs. You think you’re private? You’re just trusting a black box written by people who probably don’t even understand their own math. It’s theater. It’s not security. It’s illusion.
Sabbra Ziro
I love how this explains the power of Merkle trees so clearly. It’s not just about efficiency-it’s about empowerment. You don’t need to be a node operator to verify your own data. That’s democracy in action.
And the fact that you can prove you don’t own something? That’s revolutionary for privacy. It means you can prove your innocence without revealing your whole life. That’s huge.
Thank you for writing this. I’m sharing it with my niece who’s studying computer science.
Emily Hipps
Y’all are underestimating how much this matters. Merkle trees let regular people interact with blockchain without needing a supercomputer. That’s not just tech-that’s inclusion.
And Solana’s state compression? That’s the future of NFTs. Imagine millions of digital collectibles without the gas fees. That’s not a gimmick. That’s liberation.
Let’s keep building this stuff. The world needs it.
Kip Metcalf
Yeah, Merkle trees are cool and all, but let’s be honest-most people don’t care. They just want to buy crypto and flip it. This stuff is for the nerds.
But hey, if it keeps the chain running, I’m not complaining. 🤷♂️
Dennis Mbuthia
What a bunch of overhyped nonsense. Merkle trees? We had this in 1997 with PGP. Blockchain people just took old tech, made it slower, added coins, and called it innovation. America’s tech scene is falling apart. We used to build things. Now we just rebrand hash functions and call it a revolution.
And don’t even get me started on ZKPs-those are just magic tricks for people who don’t understand math. China and Russia are building real systems. We’re just selling vaporware.
Veronica Mead
It is imperative to note that the reliance upon SHA-256 as a cryptographic primitive within the context of Merkle tree implementations constitutes a non-trivial vulnerability vector, particularly when one considers the potential for algorithmic cryptanalysis or future computational paradigms such as quantum computation. The foundational assumption of collision resistance, while currently empirically valid, remains contingent upon the continued integrity of the underlying hash function. To assert the absolute security of the system is, therefore, an epistemological overreach.
Mollie Williams
There’s something poetic about a tree made of hashes. Each branch, a consequence of what came before. Each leaf, a moment in time, frozen in computation. The root doesn’t remember the details-but it knows if anything changed.
It’s like memory itself. We don’t store every experience. We store the checksum of who we are. And if the checksum changes? We know something’s off.
That’s why this works. It’s not just code. It’s philosophy.
Ritu Singh
They’re hiding something. Merkle trees are a distraction. The real power is in the centralized nodes that generate the proofs. Who controls those? The government? The Fed? Big Tech? The blockchain is a lie. The root is controlled by a handful of servers in Nevada. You think you’re decentralized? You’re being watched. Every proof you verify is logged. Every transaction you check is tracked. They’re using Merkle trees to make surveillance efficient. It’s not security-it’s control.
Dave Lite
Wait, so if the Merkle root changes, it means someone tampered with the data? But what if the node you’re querying is malicious? They could give you a fake root.
So you’re trusting the node to give you the right root? That’s the whole problem.
How do you know the root you’re checking is the real one?
Jennah Grant
Because the root is published in the block header, which is signed by miners and verified by every full node on the network. You don’t trust one node-you trust the consensus. If the root is fake, the whole block gets rejected. That’s the whole point of decentralization.
It’s not about trusting one person. It’s about trusting the math, the network, and the incentives.